How to Set Up an Email Proxy for Better Online Privacy

Some say email is an old-school technology that is pushed out by newer communication methods. In reality, email is being used by billions of people worldwide, and the number keeps on growing. Alongside personal communication, email marketing is a profitable conversion channel that is also a great brand awareness tool.
On the other hand, malicious actors exploit email vulnerabilities. Sending spam promotional letters is only one side of the coin; meanwhile, phishing emails can be particularly dangerous. With the rise of AI technology, cybercriminals can forge convincing fraudulent phishing mail in multiple languages filled with infectious backlinks and attachments.
That's why protecting your email accounts is paramount. One way of doing so is by using an email proxy server to mask your original IP address. In this article, we'll explain how to set it up for online privacy protection.
What Is an Email Proxy?
Imagine an email proxy server as an intermediary that can perform various actions before an email is sent to or received by the recipient. In a standard online email communication, a user sends an email from the original IP address to the recipient's IP. Although indirectly, there is a way to deduce the sender's IP, which can then be used to target it with cyber attacks, like email bombing.
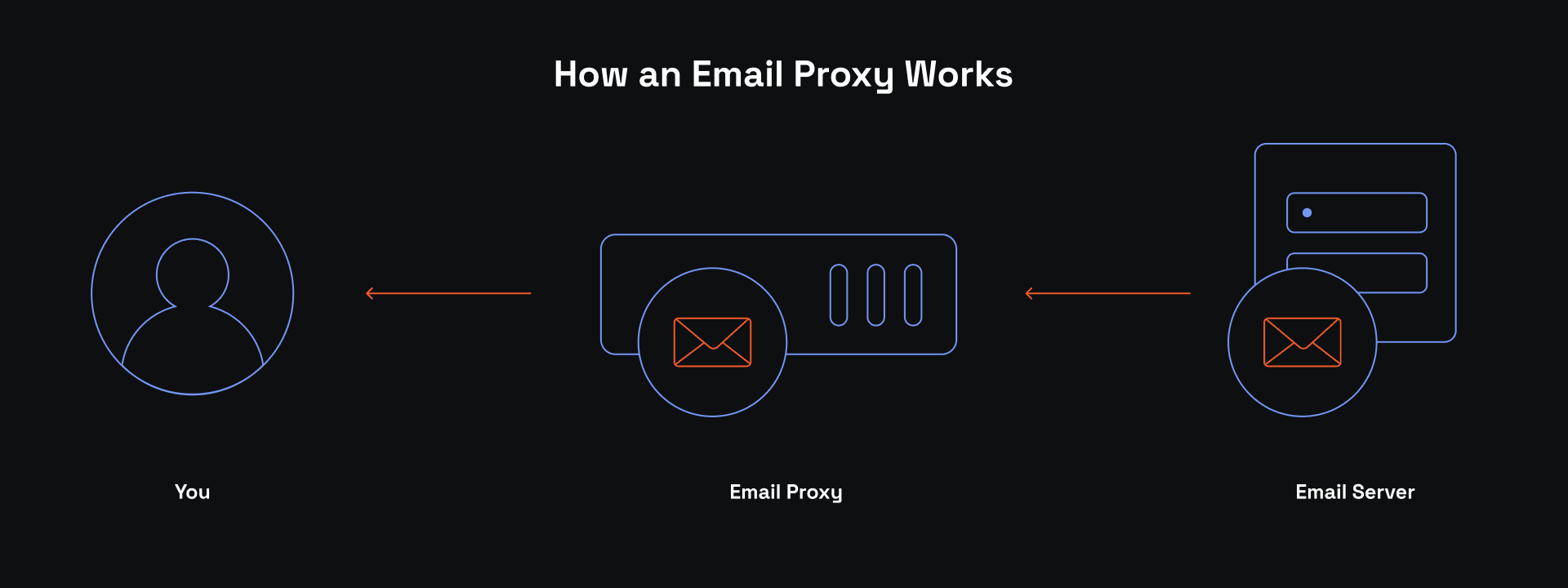
An email proxy server stands between the sender and the recipient. The email is first sent to the proxy email address, which then forwards it to the recipient. This way, it masks the original IP address and assigns an alternative to improve email security. Depending on the configuration, these proxy servers can defend against phishing attacks and limit the flow to avoid overloading, verify senders' addresses, encrypt the content, and more.
Common Types of Email Proxies
In simplified terms, a proxy server is nothing but a third-party machine configured to fulfill specific tasks. That's why this technology has a broad use case spectrum. IT professionals and tech-savvy internet users can shape email proxies according to their demands, leaving plenty of room for customization. Let's overview the most common types of email proxies you may encounter.
SMTP Proxies
SMTP stands for Simple Mail Transfer Protocol, and it is the current standard protocol for managing online mail data flows. At a user level, it is generally used to control outgoing emails to mail servers, but it can also be configured to accept incoming data to clients. However, you will encounter IMAP/POP3 protocols for receiving emails most of the time, which we’ll explain below.
An SMTP proxy is a server that manages data transfers between email clients and mail servers. Although it uses the dedicated SMTP protocol, it's worth noting it utilizes the Transmission Control Protocol (TCP) for timely and accurate email deliveries. Simultaneously, you don't need an SMTP proxy for a successful email exchange, but it adds valuable benefits like security and rate limiting.
Here's a step-by-step process of how SMTP proxies work:
1. A user writes an email on their email client (Gmail, ProtonMail, etc.)
2. The client sends it to the local mail server.
3. The local mail server connects to an SMTP proxy via SMTP protocol and routes the email to it.
4. At this stage, an SMTP proxy can perform various tasks, like encryption, malware scanning, authentication, etc.
5. SMTP proxy connects to a destination mail server via SMTP protocol.
6. The email is sent to the destination mail server.
7. The mail server then forwards it to the correct recipient on its network.
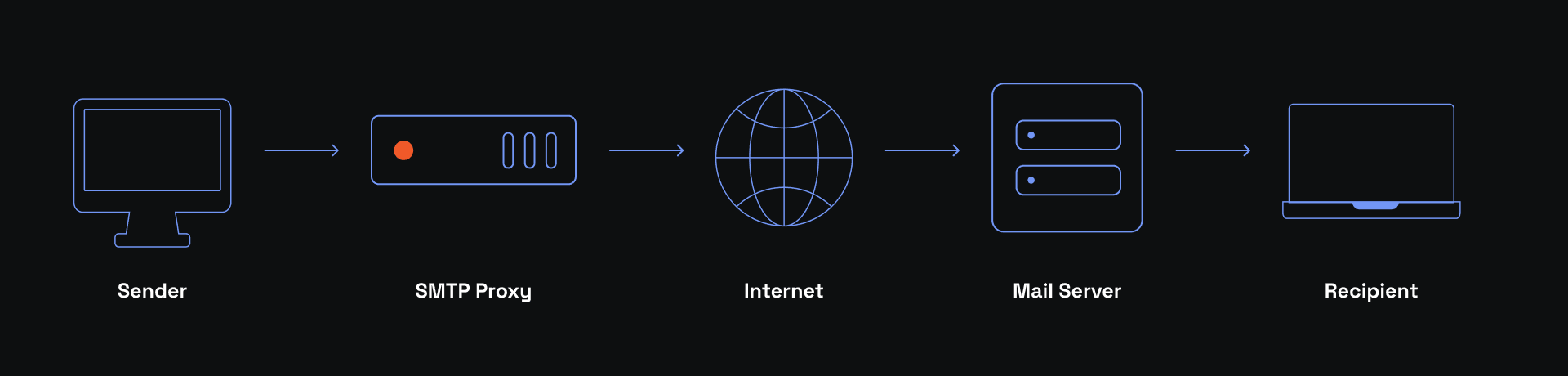
Without an SMTP proxy, there would be no steps 3 to 5. As you can see, step 4 may include encryption and malware detection, so it is beneficial for senders and recipients' online privacy protection and cybersecurity in general.
IMAP/POP3 Proxies
While SMPT is primarily used for sending emails (and very rarely for receiving), the IMAP and POP3 protocols are widely deployed to retrieve emails from email clients.
IMAP stands for Internet Message Access Protocol. It’s cloud-based and stores emails on online servers, frequently in data centers. A user can access these emails on any device, and any changes made to them are synced on all devices. In other words, it provides cross-device email access.
POP3 stands for Post Office Protocol 3. Unlike IMAP, this protocol downloads all emails to the user's device and deletes them from the mail server. This way, the user can only access them on one device, but it also means that emails cannot be tampered with or stolen if the mail server is breached.
The IMAP/POP3 proxies are similar to SMTP proxies but work with these 2 protocols. They intercept IMAP/POP3 traffic and, depending on customization, provide malware scanning, spam filtering, encryption, and routing optimization.
How Does It Differ From a VPN?
At first glance, proxies and VPNs may seem a similar technology. Both reroute user traffic through a third-party server and obfuscate original IP addresses. However, the more you look, the more differences you'll notice, so proxies should be distinct from VPNs.
Firstly, business VPNs are primarily used for secure remote access to corporate networks. Whenever a user wants to use business resources remotely, they connect to a VPN. It assigns a new IP address that is whitelisted on the business network and establishes an encrypted tunnel to protect against espionage.
Consumer-centric VPNs also obfuscate user IP addresses but, in this case, to protect against IP-based cyberattacks and surveillance. They reroute user traffic from the ISP to the VPN server and encrypt it so that ISP, governments, or any other surveillance agencies cannot monitor online activities. Such VPNs usually have strict no-logs policies, which means they do not collect, store, share, or sell user data.
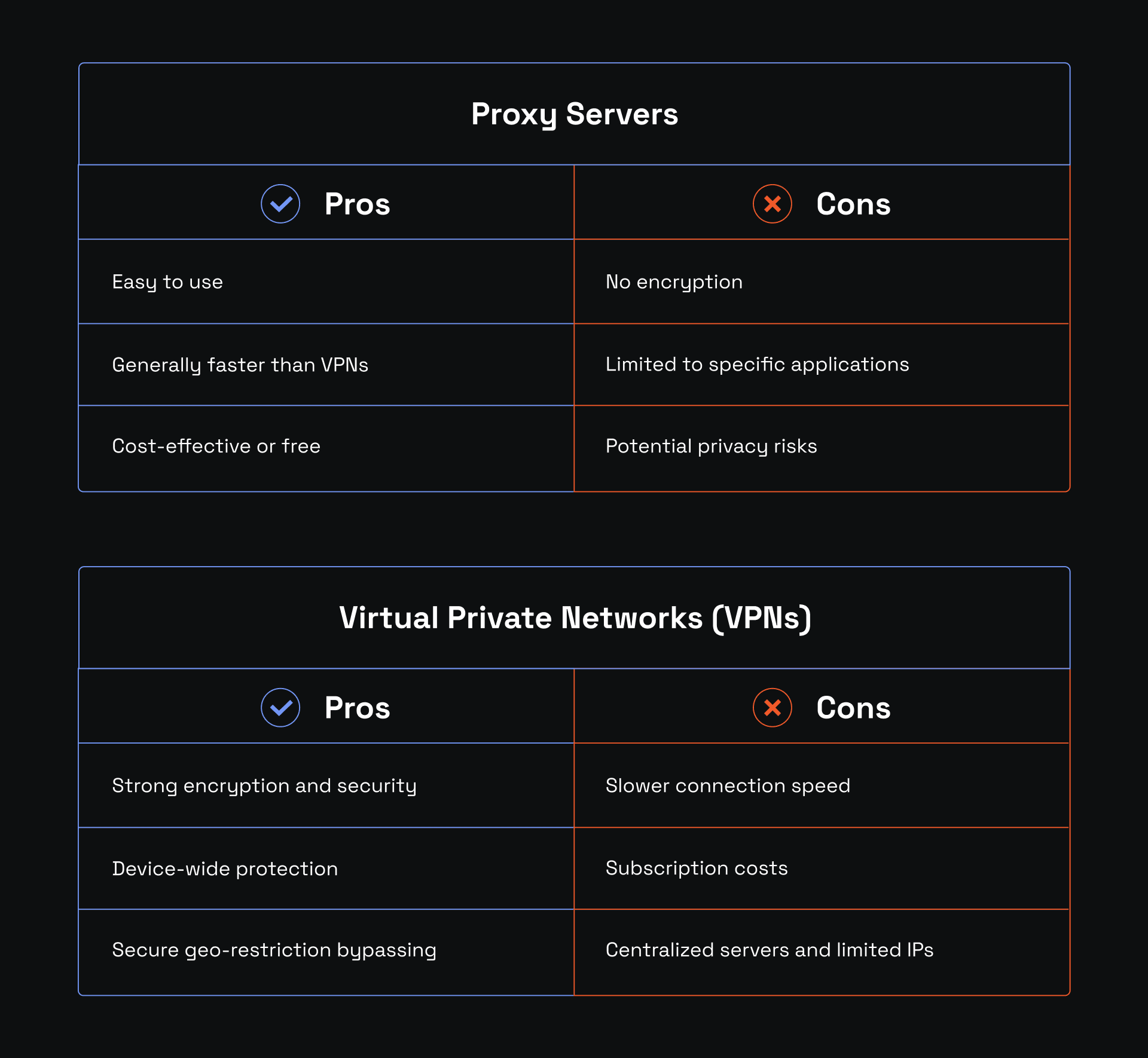
Typically, proxies do not apply encryption by default or offer a no-logs server structure. They can be customized to perform these actions, but that requires additional effort. Instead, they are a more versatile technology that is used for routing optimization, data filtering, rate limiting, and load redistribution.
Benefits of Using an Email Proxy
The SMTP, IMAP, and POP3 proxies provide essential benefits for both email sender and recipient. Let's overview the most common email proxy server benefits one by one.
Enhanced Privacy & Security
Whether on a local network or the World Wide Web, additional encryption is beneficial to hide email content from third-party spectators. SMTP proxies that encrypt emails make them indecipherable until they reach the intended recipient, so the communication happens only between two authorized parties.
Another key benefit is email security. SMTP, IMAP, and POP3 proxies can perform virus scanning, protecting the recipient before malicious content infects their device. For example, if cybercriminals massively bombard a specific email client with phishing attacks that include malicious backlinks or attachments, email proxy servers can filter out and block these threats.
Email Traffic Management
Most of us have experienced email spam and the frustration when it gets out of hand. It's not always malicious, as numerous marketing companies bombard users with promotional letters. However, cybercriminals also flood email clients aiming to overload and take down their servers, called denial-of service cyberattacks.
Rate limiting is one of the crucial email proxy server functions. It enforces strict rules about email traffic flow, like the number of emails that can reach the recipient or be sent towards an email client in a specific timeframe. It can also redistribute email flow across multiple servers to lighten the load on all of them.
Compliance and Anonymity
Masking email content is significant in terms of the most sensitive information. For example, the Health Insurance Portability and Accountability Act demands healthcare service providers ensure client confidentiality. One way of doing so is deploying email proxies that encrypt all content before sending it to the target recipient. The same applies to legal and financial emails.
Prevent Email Blocking
Marketing professionals often use emails to reach clients or promote services to new potential buyers. Occasionally, some marketing agency mail clients can get banned or flagged as spam if they overdo it. In this case, an email proxy issues an alternative IP address and applies spam filtering to ensure future emails look legitimate and reach their target audience.
Common Use Cases for Email Proxies
Now that we've laid out the theory, let's overview the exact email proxy server use cases. Here are four scenarios that can benefit businesses and individuals at the same time.
Email Marketing Campaigns
Proxy email address is a great email marketing tool. Because it obfuscates senders' IP addresses, it can avoid IP-based spam filtering to improve delivery rates. Simultaneously, many IPs used for marketing are blacklisted, so a new batch of fresh ones allows for continuing the marketing campaign. Keep in mind that residential proxies offer hundreds of thousands of high-quality IPs that can replace the ones flagged for spam.
Corporate Email Security
The communication over the local corporate network must be protected from external and internal threats. In fact, human error is the primary cause of most cyber incidents. Employees may click on a fraudulent phishing backlink or download an infectious attachment, risking the safety of all connected devices. An email proxy server placed in front of the company's computer network can host a firewall or antivirus to identify threats before they reach the recipient, significantly reducing hacking risks.
Automated Emails
Running a successful marketing campaign is nearly impossible without email automation. Instead of using the same business IP address and risking getting banned, email proxies provide thousands of high trust score IPs to increase delivery rates. Simultaneously, you can create multiple proxy email addresses to spoof the original sender's address.
Anonymous Communication
Journalists, whistleblowers, and political activists require robust online privacy protection to avoid governmental censorship and, in extreme cases, arrest. Popular email clients like Gmail are obliged to comply with the law, so it's best to use an alternative proxy email address and an additional email proxy to apply encryption and obfuscate the original sender's IP.
How to Set Up an Email Proxy
The exact workflow of setting SMTP, IMAP, and POP3 email proxies depends on the chosen service provider, so you'll have to double-check their manuals for a step-by-step guide. However, if you're looking to use proxies with standard email clients like Gmail, here's how to do it using the MarsProxies browser extension.
1. Go to the Chrome Web Store and add the MarsProxies browser extension.
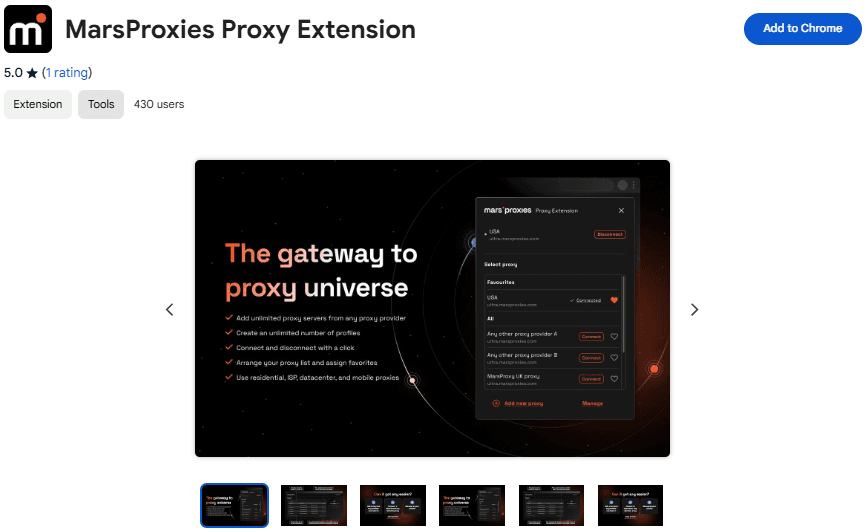
2. Pin the extension to the menu so that you can find it quickly. Click on it and select Add new proxy.
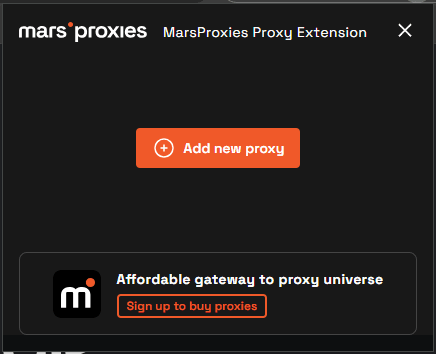
3. Now, you have to visit your MarsProxies dashboard to generate the required proxies. Follow this guide on how to do it.
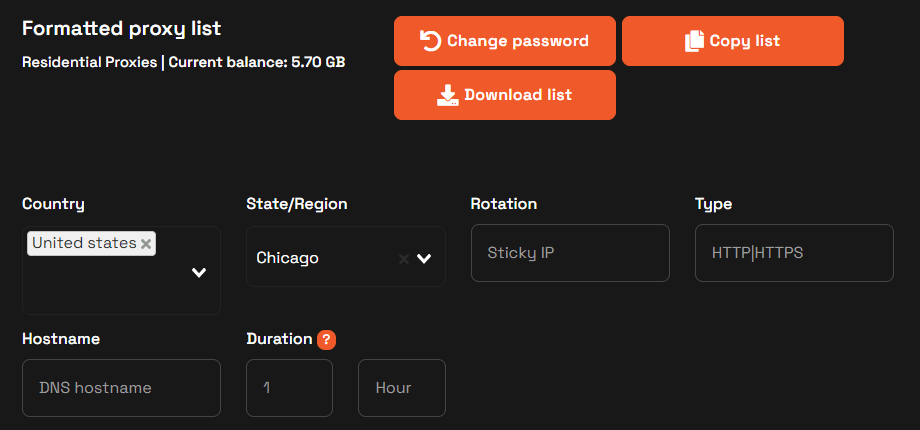
4. Scroll down until you see the proxy list and copy the string, as seen in the image below.
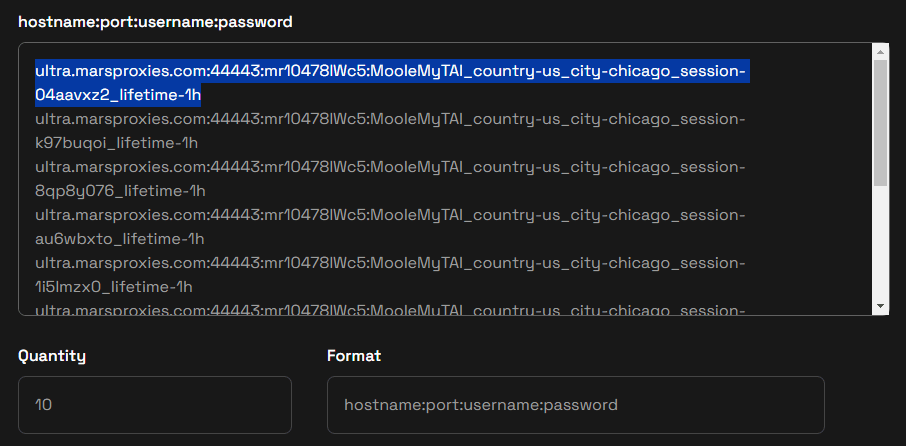
5. Go back to the MarsProxies extension and paste the copied string into the Hostname field. The remaining fields will be filled automatically.
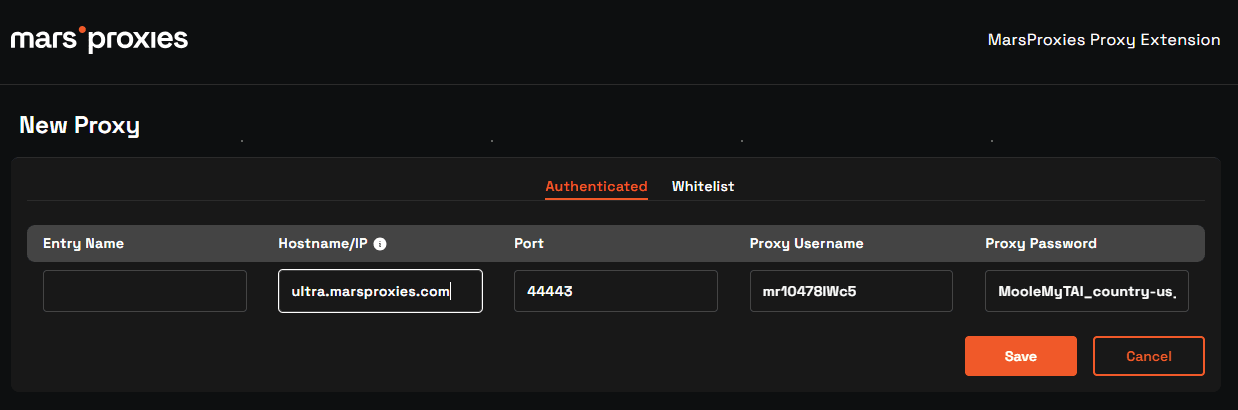
6. Pick a name for your proxy connection and click Save.
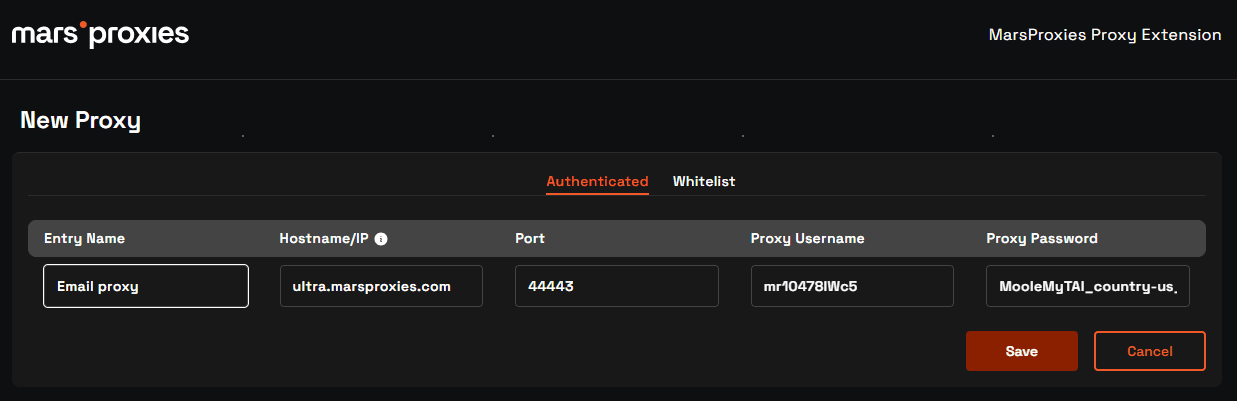
7. Your saved option will appear in the extension proxy list. Click on the Connect button next to it, and you're all set!
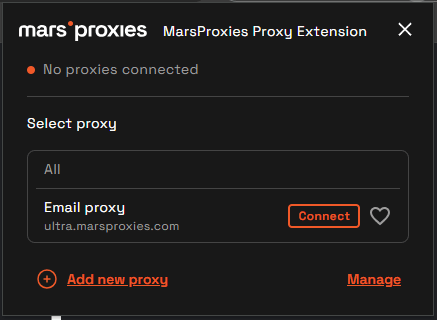
Now, all your Chrome browser traffic, including the Gmail email client, is forwarded via a proxy connection.
Choosing the Right Email Proxy Service
The best email proxy service provider depends on your specific needs. For example, some services may focus on spam filtering and load redistribution, while others are optimized for creating dozens of proxy email addresses. Here's what you should consider before subscribing.
- IP address pool
A vast proxy server network is paramount to providing you with the required number of IP addresses. Consider rotating residential proxies if you're planning an email marketing campaign. Simultaneously, a large pool lets you create a proxy email address with a different IP whenever you need one.
- Security features
Businesses and individual internet users will be much safer online if SMTP proxies apply encryption and filter out malicious mail. Verify your email proxy provider offers these services if you're looking for an extra layer of email security.
- Simplicity and price
Not everyone is a tech guru, and email marketing specialists don't have to know the ins and outs of encryption cryptography. Seek services that are user-friendly and affordable so that you can make the most of your email proxies without overpaying.
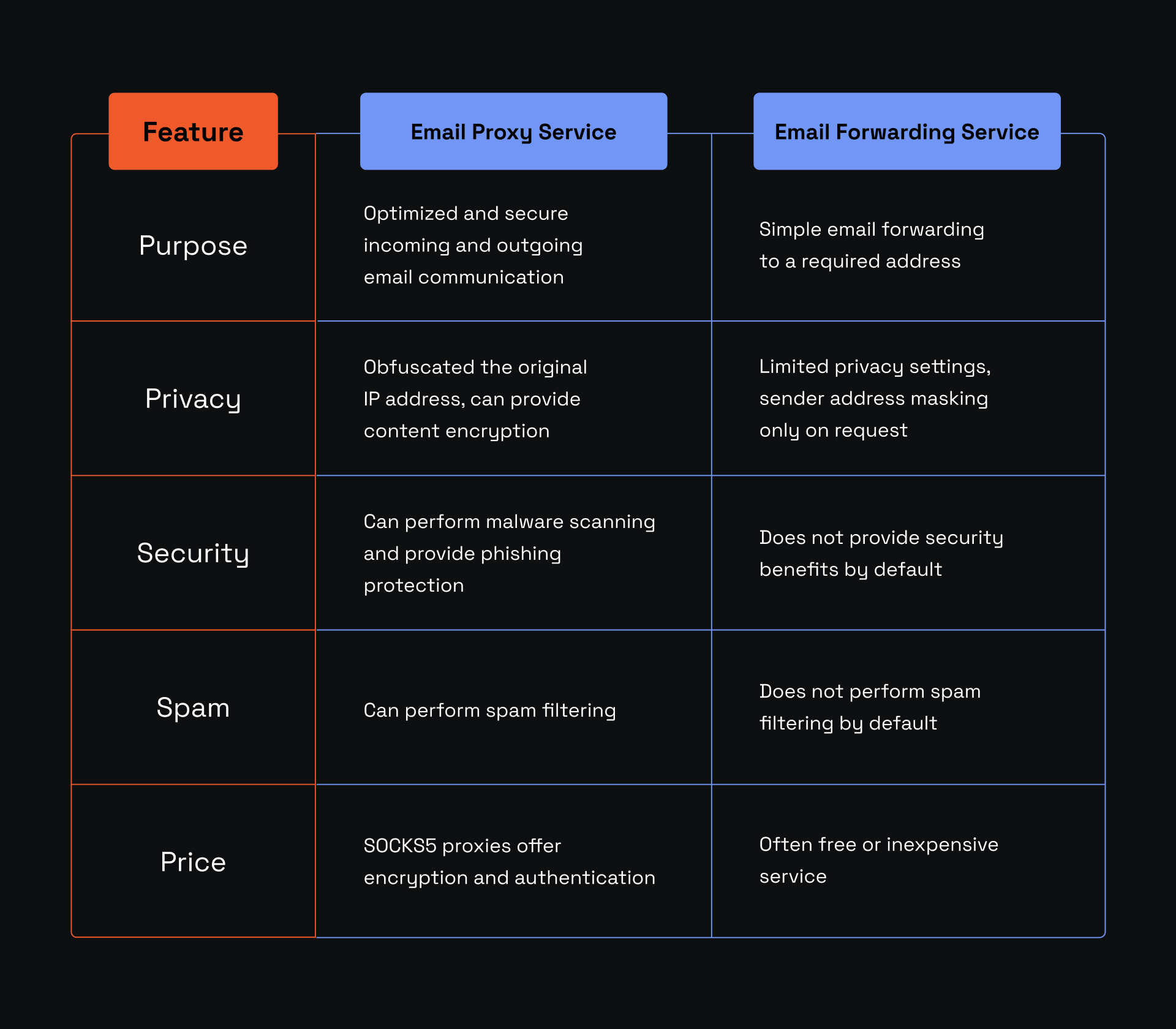
Email Proxy vs. Email Forwarding Services
Email proxies are sometimes confused for email forwarding services because both work with email routing to the target recipient. If you're wondering which service you require, take a look at the table below for a side-by-side comparison.
Conclusion
Although email proxies are less widespread than residential or datacenter proxies for web scraping, marketing research, or geo-block evasion, they provide valuable security benefits. Simultaneously, this technology is paramount for automated email marketing campaigns that utilize a proxy email address to avoid detection and bans.
It is always best to remain within ethical boundaries, so avoid sending spam mail and consider how your content benefits the receiver, and email proxies will optimize the delivery rates.